A system administrator or network engineer may face a situation when he needs to access the resources of network from the public Internet, hidden behind a NAT and protected by a firewall.
To solve this problem, sysadmins can use TeamViewer or some other remote access tool. But there is a simpler solution that does not require third-party software other than the OpenSSH package.
What is an SSH tunnel?
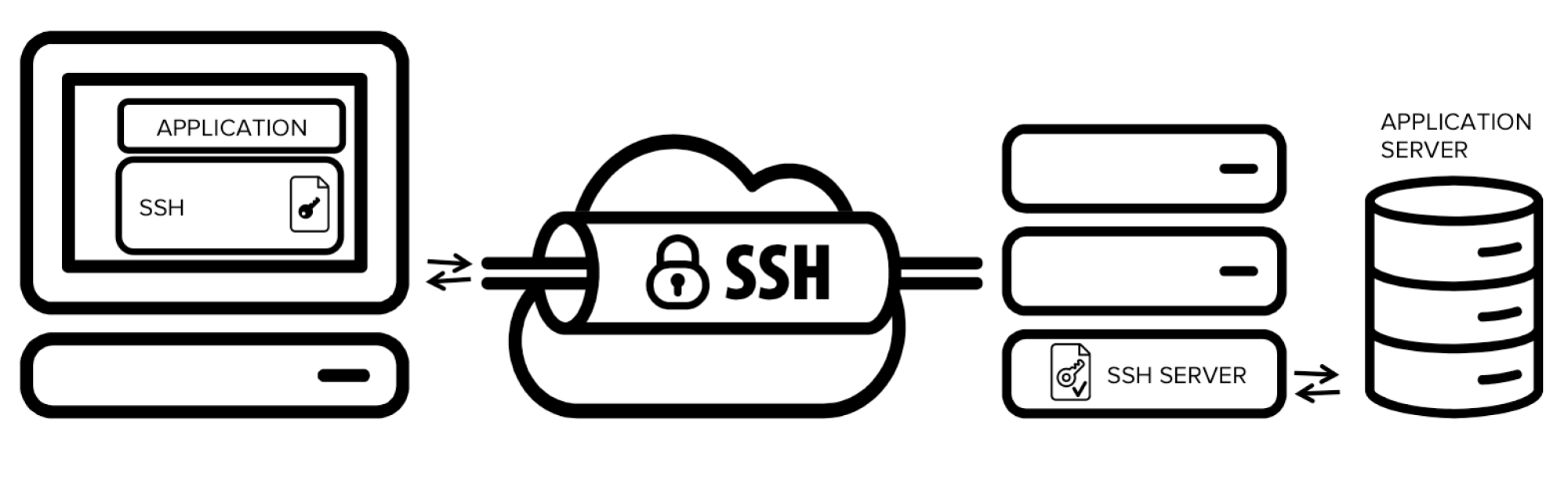
SSH or Secure Shell is a protocol for secure working on the network. The unique thing about SSH is that the traffic is not just proxied, but this fact is carefully concealed. Unlike a standard proxy, an interception from the outside is eliminated, and the secrecy of personal data is guaranteed.
The technology is used for opening a backdoor into private networks, bypassing firewalls, and channel encryption.
Creating a tunnel with an SSH is the easiest and fastest way to establish encrypted channel. To set up such a tunnel, you need a computer with an SSH server and another computer with an SSH client. The technology is available on any PC running the Linux OS. As for Windows, he OpenSSH server is on Windows Server 2019 and the client - on Windows 10.
Creating an SSH Tunnel
You need two keys. The public key is stored on the server while the private key is on the local machine.
Ubuntu and other Linux/macOS distributions
Start a terminal and run the command:
ssh-keygen -t rsa
You will see a dialog box in the terminal:
Enter file in which to save the key (/home/user/.ssh/id_rsa):
By default, the private part is saved in the .ssh folder in the file id_rsa. You can specify a different address and filename.
The system will then suggest creating a password for extra security for the key. This is to protect the key so that it cannot be used by anybody with access to the local machine. If you don't need a password, leave the field blank and press Enter.
Enter passphrase (empty for no passphrase):
After the successful creation of the key pair, the following message will appear in the terminal::
Your identification has been saved in /home/user/.ssh/id_rsa.
Your public key has been saved in /home/user/.ssh/id_rsa.pub.
The key fingerprint is:
476:b2:a8:7f:08:b4:c0:af:81:25:7e:21:48:01:0e:98 user@localhost
copy the public key and add it to the remote machine. You can open the file /home/user/.ssh/id_rsa.pub with any text editor or display its contents in the terminal:
cat ~/.ssh/id_rsa.pub
Copy the key and add it to the server. Make sure that there are no spaces or hyphens in it.
You can copy the public key automatically using the command:
ssh-copy-id user@remoteserver
In the final step, create an SSH tunnel to the remote server.
Run the command
ssh root@HOST
HOST is the public IP address of the server.
The first time you connect, the system will warn you about the unknown host and ask if you trust it. Enter 'yes' and press Enter.
Windows
There are two ways to generate a key pair on Windows - via the PowerShell console, or by using PuTTygen (installed together with PuTTy).
To generate the keys via PowerShell, open a terminal and run
ssh-keygen -t rsa
Protect the private key with a password or leave the field blank and press Enter.
By default, the public key is stored in ~/.ssh/id_rsa.pub. The private key, named id_rsa, is in the same folder. Open the public key file with a text editor or use the cat command in PowerShell:
cat ~/.ssh/id_rsa.pub
Copy the public key and add it to the remote server.
To connect to the server, run:
ssh root@HOST
The HOST parameter is the public IP address of the remote server to which you added the public key.
The first time you connect, the OS will warn you about the unknown host and ask if you trust it. Enter 'yes' and press Enter.
Difference between SSH and VPN
A VPN allows users to connect to the Internet through a private network, providing a secure online browsing experience. With this technology, you can instantly connect remotely to a server from any location.
The VPN encrypts traffic to preserve digital privacy. This added layer of encryption ensures that intruders, hackers, and third-party website trackers cannot monitor network traffic information. Consequently, the VPN works on a broader level than SSH tunnels.
SSH tunnels work at the application level. They are manually configured every time you want to encrypt network traffic. Also, compared to VPNs, SSH tunnels are more difficult to set up and slow down connection speeds.




