The cloud security landscape has fundamentally shifted. While organizations once focused primarily on patching servers and fortifying infrastructure, today's attackers have found a more accessible target: user credentials.
The most critical cloud security flaw is no longer in the cloud itself—it's in how users access it.
This reality became painfully clear in 2024 when high-profile breaches affecting Snowflake customers, including Ticketmaster and Santander, made headlines worldwide. The root cause wasn't a sophisticated exploit of cloud infrastructure. It was something far simpler: compromised credentials and the absence of basic access controls.
The Shared Responsibility
These incidents serve as a stark reminder of the shared responsibility model that governs cloud security. Cloud providers secure the underlying infrastructure—the physical data centers, networks, and platform services. However, customers bear unequivocal responsibility for securing their own access controls, user identities, and data.
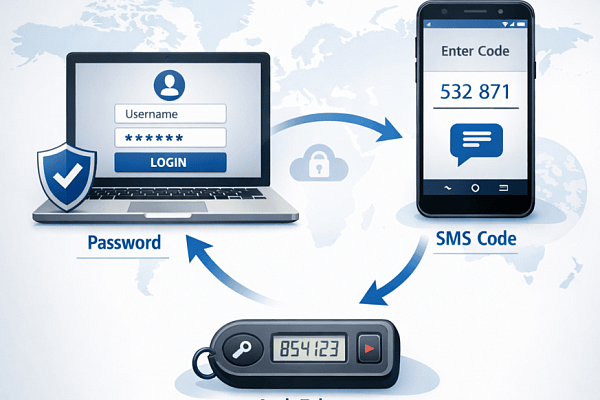
The common point of failure? Customer-side security practices, specifically the lack of Multi-Factor Authentication on critical accounts and service credentials.
When attackers obtain single-factor credentials through phishing, data leaks, or brute force attacks, they effectively hold a master key. Even the most secure cloud platform becomes vulnerable from the inside when accessed with legitimate-looking credentials.
Mandating a Zero Trust & MFA Posture
Organizations must adopt the Zero Trust principle: never trust, always verify. Every access attempt should be authenticated and authorized, regardless of where it originates.
Within this framework, MFA stands not as a recommended best practice but as an absolute baseline requirement. It remains the most effective immediate action to neutralize threats from stolen, phished, or leaked passwords. A compromised password alone becomes useless without the second authentication factor.
Identity has become the new security perimeter and the primary attack vector for malicious actors targeting cloud environments. We urge all organizations to audit their cloud access controls immediately, enforce MFA universally across all accounts, and embrace the shared responsibility model proactively rather than reactively. In today's threat landscape, securing identity is synonymous with securing the cloud.