DDoS Protection (WAF)
A successful DDoS attack can cripple your online services, leading to significant revenue loss and customer dissatisfaction. Our DDoS protection service is a robust defense mechanism designed to mitigate a wide range of attacks, including TCP/SYN floods, ensuring your business remains operational and secure.
The solution integrates seamlessly with your existing infrastructure hosted on the Cloud4U platform.
Get comprehensive protection without the need for complex data migration, additional configuration, software installation, or costly hardware purchases.
How Our DDoS Protection Works
Cloud4U provides a multi-layered defense strategy with two core levels of protection:
Level 1: Network-Level Protection
Our system filters incoming traffic at the network edge (L3/L4), blocking malicious packets before they can congest your bandwidth. This ensures only legitimate requests reach your servers.
- A dedicated IP address or cluster from a protected subnet is assigned to your service.
- Our infrastructure accepts and scrubs all incoming traffic directed to this IP.
- You receive a continuous stream of cleaned, legitimate traffic.
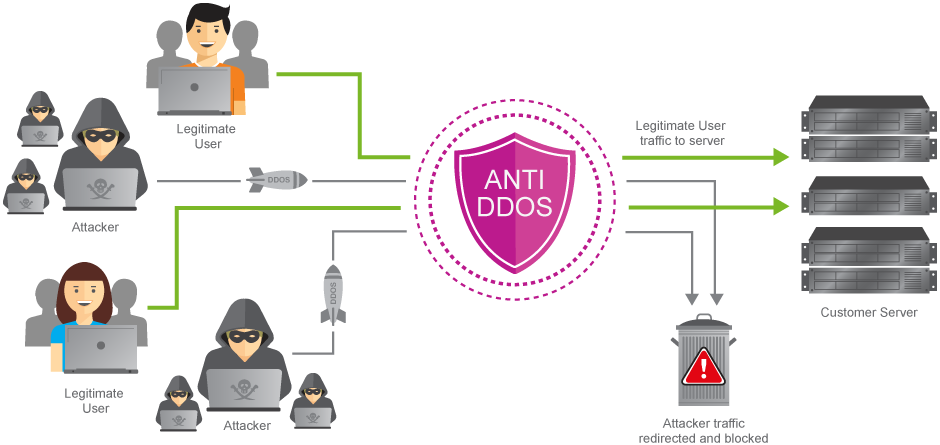
Level 2: Application-Level Protection (WAF)
For advanced threats, our Web Application Firewall (WAF) provides deep traffic inspection at the application layer (L7). It analyzes HTTP/HTTPS, DNS, and SIP protocols to block sophisticated attacks targeting web application vulnerabilities.
This solution helps you comply with PCI DSS security standards, reduces application-level threats, and safeguards sensitive corporate and customer data from theft and manipulation.
Furthermore, it helps prevent your infrastructure from being exploited to launch attacks on other networks.
Key Benefits of Choosing Cloud4U
- Cost-Effective. Select a tailored protection level that fits your specific requirements and budget.
- Elastic Scalability. Our platform is built to simultaneously mitigate multiple, large-scale DDoS attacks.
- Proven Reliability. A fault-tolerant filtering system ensures attack traffic is effectively neutralized without impacting legitimate users.
- 24/7 Continuous Monitoring. Our security team provides round-the-clock surveillance to ensure constant protection.
- Deep Expertise. Leverage Cloud4U's specialized knowledge in securing cloud environments.
Plans & Prices
Standard
Dedicated IP-address
WAF Connectivity
L7 Attack Reports
Third-Party SSL Certificate Support
Legal Entity Contract (Upon Request)
Premium IP Address
Blacklists/Whitelists: Up to 5 Rules
Load balancing: Up to 2 servers
Ticketing Support Response: < 30 minutes
146 $ per month
Excluding VAT
Professional
Protection for 3 Domains
High-Priority Traffic Processing
ache Reset by Mask
Detailed L7 Attack Reports
Web Application Firewall
API Integration
Traffic Anomaly Alerts
Blacklists/Whitelists: Up to 50 Rules
Load balancing: Up to 10 Servers
Support Response Time: < 15 minutes
320 $ per month
Excluding VAT
Enterprise
Protection for 10 domains
Unlimited: geo-blocking and use of WAF
Possibility to include your IP networks in the protection
Best suited for IP-TV connection
The top priority for traffic processing
Role-based account management
L7 level attack reports
Support for mobile phone alerts
BGP protection connectivity
Individually tailored page
Blacklists/Whitelists: up to 100 rules
Load balancing: any number of servers
Expert support
Response time: less than 10 minutes
800 $ per month
Excluding VAT
FAQ
A DDoS attack typically unfolds in two key stages:
- Botnet Recruitment: An attacker first assembles a network of compromised computers and devices (a botnet). This distributed network allows them to generate an attack of massive scale.
- Resource Saturation: The botnet is then directed to send a flood of requests to the target. The volume of this malicious traffic overwhelms the server's performance and network bandwidth, causing the web resource to crash or become unresponsive.
DDoS attacks can target various layers of the OSI model, each with its own protocols and functions. Common attack vectors include:
- Volumetric Attacks (Layers 3 & 4): These attacks target the network and transport layers, consuming bandwidth with massive traffic floods (e.g., UDP floods, ICMP floods).
- Protocol Attacks (Layers 3 & 4): These exhaust the resources of network infrastructure like servers or firewalls (e.g., SYN floods, Ping of Death).
- Application Layer Attacks (Layer 7): These target the application layer itself, disrupting specific functions of web applications (e.g., HTTP floods, attacks on DNS servers). These are often more sophisticated and harder to detect.
DDoS attacks are generally categorized by their method and target layer:
- Network Layer DDoS Attacks: These include flood-based attacks (like synchronized SYN floods) and reflection attacks (such as UDP floods) that aim to saturate your bandwidth and infrastructure resources.
- Application Layer DDoS Attacks: These high-level attacks target the application's functionality (e.g., HTTP/HTTPS floods). They are designed to crash the application servers by mimicking legitimate user traffic, making them highly effective at causing service disruption.
A robust DDoS mitigation strategy involves a multi-layered approach:
- Proactive Monitoring & Patching: Conduct systematic software monitoring to identify vulnerabilities and perform regular firmware updates to minimize security gaps.
- Resource Scaling & Distribution: Increase server capacity and distribute resources geographically to handle sudden traffic spikes.
- Incident Response Planning: Develop and practice an incident response checklist and maintain clear communication channels with your service provider for rapid traffic filtering.
- Specialized DDoS Protection Services: Employ a dedicated DDoS protection solution that can automatically detect and filter out malicious traffic before it reaches your infrastructure. This includes techniques like rate limiting, network-level traffic filtering, and cloud-based load distribution.
The impact of a successful DDoS attack can be severe and multifaceted:
- Service Downtime: Complete or partial unavailability of your web resource, leading to direct operational disruption.
- Financial Losses: Revenue loss due to downtime, coupled with the costs of mitigation and recovery efforts.
- Reputational Damage: Erosion of customer trust and brand reputation if availability and security cannot be guaranteed.
- Data Breach and Security Risks: DDoS attacks can be used as a smokescreen to distract your security team while attackers attempt to steal data or infiltrate your systems.
- Ransom and Extortion: Attackers may use the DDoS attack for ransom, demanding payment to stop the assault.
- Legal and Compliance Repercussions: If the attack leads to a data breach, it may result in violations of data protection laws and regulatory fines.
- Loss of Customer Confidence: Persistent availability issues can drive customers to competitors, resulting in long-term business loss.
DDoS protection operates by continuously monitoring incoming traffic and filtering out malicious requests before they can overwhelm your resources. This is often delivered via a cloud-based scrubbing model, eliminating the need for any specialized on-premises hardware. A comprehensive DDoS protection service typically includes customizable traffic monitoring and filtering rules, backed by a dedicated team of security experts with hands-on experience in mitigating cyberattacks.
The cost of DDoS protection services varies based on the level of security, the provider, and the required resources. Typical service tiers include:
- Basic Protection: Ideal for small to medium businesses.
- Advanced Protection: For enterprises with higher traffic volumes.
- Premium Protection: Designed for mission-critical applications.
The final price is influenced by key factors such as your expected traffic volume, the sophistication of the attack vectors you need to defend against, the chosen service provider, and the overall complexity of your IT environment.
You can recognize a potential DDoS attack by several key indicators:
- A sudden, unexpected surge in traffic to your website or application.
- Severely degraded performance or timeouts, making your service slow or unresponsive.
- A high number of connection requests originating from a single IP address or a narrow range of IPs.
- An abnormal amount of non-standard or malformed requests that don't resemble legitimate user behavior.
- A sharp increase in server errors, such as HTTP 500 or 503 status codes.
- Unusual spikes in database load or application errors recorded in your server logs.
A Content Delivery Network (CDN) plays a crucial role in a multi-layered DDoS protection strategy. By distributing traffic across a global network of servers, a CDN can absorb and disperse attack traffic, preventing it from concentrating on and overwhelming your origin server. This is particularly effective against volumetric attacks and for protecting websites that rely heavily on static content, as the CDN can cache and serve this content, filtering out malicious GET requests at the edge.
