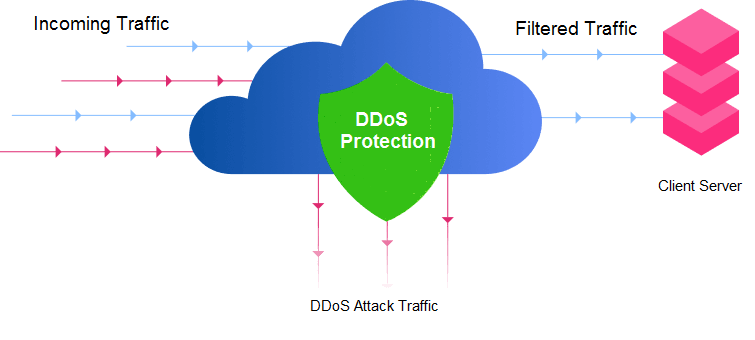
DDoS protection
Professional protection against DDoS attacks
AntiDoS from Cloud4U easily integrates with your infrastructure hosted in our cloud based on IaaS model, does not require data transfer and additional configuration, software installation or hardware purchase. Cleanup options are tailored specifically to your facility's requirements.
The service is based on DDoS Guard. The price is specified without initial payments for installation and setup.
How it Works?
Cloud4U operates a geo-distributed traffic filtering network with direct connections to TIER-1 operator networks, ensuring fast and reliable filtering of incoming traffic. Our filtering nodes are strategically located in:
Amsterdam, the Netherlands
Frankfurt, Germany,
Tokyo, Japan,
Washington, USA
This global topology enables efficient local traffic filtering at scale, preventing excessive load on core networks and maintaining connectivity even during attacks.
Types of DDos protection
Basic DDoS Protection – Network-Level Defense
Cloud4U’s filtering modules block malicious traffic, allowing only legitimate requests to pass through preventing bandwidth saturation. During an attack, you’ll be assigned a dedicated IP (or cluster of IPs) from a protected subnet. Our system, powered by industry-leading DDoS mitigation hardware, scrubs all traffic directed to these IPs, ensuring only clean traffic reaches your infrastructure.
Our always-on filtering detects and blocks all known DDoS attack types from the very first malicious packet or flow.
Advanced Protection – Application Layer Defense
All connections to your applications pass through our Web Application Firewall (WAF), which analyzes and sanitizes traffic for HTTP/HTTPS, DNS, SIP, and other application-layer protocols. The WAF is customized to your application’s unique requirements.
This solution ensures fast, secure, and reliable delivery of critical web applications while mitigating vulnerabilities. It meets PCI DSS security requirements, provides protection for sensitive corporate and customer data, reduces the risk of your infrastructure being hijacked for attacks.
Prices
Cost of DDoS filtering services
|
Guard Start
|
Guard 10
|
Guard 20
|
Guard 50
|
Guard 300
|
Guard Unlimited
|
|
|---|---|---|---|---|---|---|
| DDoS attack load |
1 Gb/sec
|
1 Gb/sec
|
3 Gb/sec
|
10 Gb/sec
|
10 Gb/sec
|
unlimited
|
| Traffic load after cleaning |
3 Mbit
|
10 Mbit
|
20 Mbit
|
50 Mbit
|
300 Mbit
|
unlimited
|
| SLA |
95%
|
97%
|
97%
|
99%
|
99%
|
99%
|
| Response time to request for technical support |
30 minutes
|
30 minutes
|
30 minutes
|
30 minutes
|
30 minutes
|
15 minutes
|
| Payment for traffic above what is included* |
0 $
|
0 $
|
0 $
|
0 $
|
0 $
|
0 $
|
| Monthly payment, $ |
91,9
|
235,2
|
305,4
|
459,6
|
637,73
|
1417
|
* - If traffic exceeds the included volume, you can upgrade to a higher plan for free.
Benefits: large detection base, fewer false positives and support from high-level specialists.
The cost of Web Application Firewall (WAF) service
|
WAF 3
|
WAF 10
|
WAF 20
|
WAF 50
|
WAF 300
|
WAF Unlimited
|
|
|---|---|---|---|---|---|---|
|
DDoS attack load |
1 Gb/sec
|
1 Gb/sec
|
3 Gb/sec
|
10 Gb/sec |
10 Gb/sec
|
unlimited
|
|
Traffic load after cleaning |
3 Mbit
|
10 Mbit
|
20 Mbit
|
50 Mbit
|
300 Mbit
|
unlimited
|
| SLA |
99%
|
99,5%
|
99,5%
|
99,5%
|
99,5%
|
99,5%
|
| Response time to request for technical support |
30 minutes
|
30 minutes
|
30 minutes
|
30 minutes
|
30 minutes
|
15 minutes
|
| Payment for traffic above what is included* |
0 $
|
0 $
|
0 $
|
0 $
|
0 $
|
0 $
|
|
Monthly payment, $ |
88,8
|
227,4
|
289,8
|
414,4
|
617
|
1084
|
* - If the traffic exceeds the included one, the transfer to the corresponding tariff is free of charge.
One-time payments
|
Service |
Cost
|
|---|---|
| Installation and setup |
70 $
|
| Connection during a DDoS attack |
116,8 $
|
FAQ
What is a DDoS attack?
How does a DDoS attack happen?
What layers of the OSI model are attacked during a DDoS attack?
DDoS attacks can target various levels of the OSI model, each with its own protocols and functions. Some of these levels and types of attacks include:
- Physical layer attacks, such as attacks on cable connections or physical devices.
- Data link layer attacks, related to exhausting the content address table, spoofing, MAC address substitution, and VLAN attacks.
- Network layer attacks, aimed at disrupting data routing and may include attacks on DNS servers.
- Transport layer attacks, aimed at disrupting data transmission between devices, including attacks on TCP and UDP protocols.
- Session layer attacks, aimed at disrupting session management, including attacks on login and logout protocols.
- Presentation layer attacks, aimed at disrupting data conversion into the required format, including attacks on encoding and protocols such as JPEG, PNG, and ASCII.
- Application layer attacks, aimed at disrupting application functionality, including attacks on HTTP, HTTPS, FTP, and SMTP.
What types of DDoS attacks are there?
How can you protect yourself from DDoS attacks?
Protection measures:
What are the consequences of a DDoS attack?
A DDoS attack can have the following consequences:
How does DDoS protection work?
What is the cost of DDoS protection?
The cost of DDoS protection can vary depending on the type of protection, provider, and resource volume.Types of DDoS protection:
The main factors influencing the cost are: resource volume, type of protection, chosen provider, and the level of complexity of DDoS protection.
.How to determine if it's a DDoS attack?
You can determine if it's a DDoS attack by the following signs:
- Sudden increase in traffic to the resource.
- Increased load on the resource, exceeding its bandwidth capacity.
- Multiple requests from a single IP address.
- Anomalous requests that do not conform to standard requests.
- Sudden increase in server errors, such as 500 or 503 errors.
- Increase in resource response time.
- Sudden increase in the number of requests to the resource.
- Sudden increase in database load.
- Sudden increase in server log errors.
What is the role of CDN in DDoS protection?
