To protect your IT system from being compromised, you need to understand the basic techniques used by hackers. In this article, we will look at brute force, one of the most common methods of cyber-attack.
What is a Brute Force Attack?
Brute force is an attempt to crack a password or encryption key. It involves trying different combinations of characters one after the other until one of them matches. It involves the use of special programs and services.
Brute force attacks are typically used to gain access to personal accounts or websites. Once inside, criminals can install malware, disable web applications or cause a massive data breach.
Brute force attacks are used by hackers to steal social networking accounts, documents, personal information, etc. Attackers can then sell databases of accounts, demand money, and commit many other illegal acts.
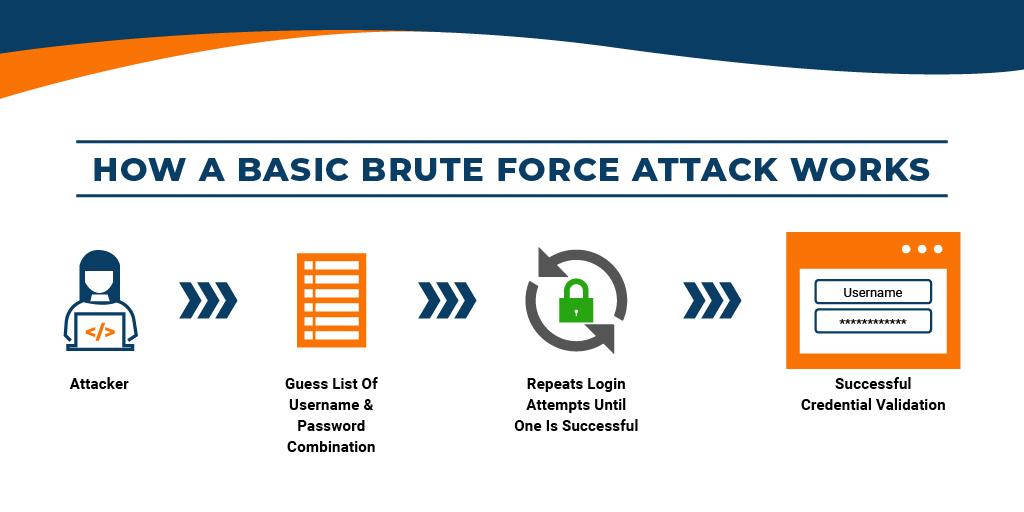
The brute force method comes in three types:
-
Gaining access to a user's personal information. The attackers learn information that helps in guessing passwords, then enter the address of the hacked resource and log in to a special program, connect a dictionary and start automatic password guessing.
-
Brute-checking - searching a database of passwords to access different accounts. When users register on websites, gaming platforms or social networks, they enter their email. The account credentials are sent to it. The attacker enters into the program the names of sites or keywords that will be used to search for emails containing logins and passwords. The cybercriminal then copies the information obtained and uses it for their own purposes.
-
Remote hacking of an operating system. Attackers use brute force and hacking utilities to gain access to someone else's PC. First, the hacker finds a vulnerable connection. The user's address can be obtained from a program or a special database. The hacker enters the dictionary and a list of IP addresses into the settings. Next, the hacker uses the obtained data and the Radmin utility (or its analogue) to control the victim's computer.
Types of Brute Force Attacks
-
Simple brute force attack. Hackers do not use any software or other tools, but try to guess your credentials logically.
-
Dictionary brute force attack. Guessing passwords by sequentially matching variations from a prepared list. The attacker builds a dictionary of the most likely character sequences and uses malware to check them one by one, trying to find a match.
-
Hybrid brute force attack. Passwords that contain multiple characters in addition to common words are cracked with a hybrid attack. This involves adding several random characters to a real word from a dictionary, which is obtained by guessing.
-
Reverse brute force attack. In this case, the hackers already know your old password. They use it to search a database of similar credentials and make calculated guesses.
-
Credential recycling. The hacker uses a previously discovered username and password and verifies it across multiple sites, suggesting that many users have the same credentials across multiple systems.
How to Prevent Brute Force Attacks
Since the principle of a brute force attack is to send multiple requests to the server at the same time, the main priority will be to identify the initiator and limit the number of requests in a given period of time. There are several ways to prevent brute force attacks:
-
Implement CAPTCHAs. This is one of the most common solutions that works for authorisation/registration forms and prevents the attacker from sending random requests.
-
Limit login attempts. This method allows you to limit the duration of client requests. As a result, the amount of time it takes to make a request is limited for both the actual user and the script.
-
Use strong passwords. The best way to protect against brute force attacks is to use strong passwords. A strong password is at least eight characters long and contains letters, numbers and special symbols. Also, do not use the same password for different services. For even better protection, use two-factor authentication.
It is important to ensure protection at the corporate level. System administrators can prevent employees from taking actions that could lead to a cyber attack. For example, many organisations disable the installation of third-party applications on workstations and other devices connected to the corporate network.
Some organisations also lock down access to online resources, allowing access only to sites that are necessary for work, and set up forced password updates in the email client every two or three months.
A brute force attack requires a system vulnerability. The more complex the IT structure, the more software a company uses, the higher the risk of hacking. Cloud server is more secure against such attacks. Therefore, migrating to the cloud can be one of the ways to reduce the risks.



